Smartphone malware has started to be increasingly prevalent, and it has become more necessary for users to be aware of how to protect their devices. The more information we store on our phones, the more reason to ensure that we protect our devices because the consequences of such loss become more significant.
But let’s face it. Users are generally careless about the latest malware and how to find out if their devices have been attacked. Take note that there are threats that are able to hide unnoticed from users’ devices. By the time the victim learns about it, the device has already been attacked – your passwords, contact information, private photos and files may have already been compromised.
There are many ways for malware to conceal itself, but once it kicks into action, you will notice signs of illegitimate activity that you should pay attention to.
Signs that your mobile device has been infected by a malware attack
Sign #1. The system or apps start behaving irregularly.
If you have apps that have suddenly failed to work even though they used to work just fine, there might have been a malware attack. Signs of strange activities are the sudden closing of the app or displaying of various error messages. This means a malicious code is running in the background and interfering with the normal processes.
When malware has taken over an app, it can take illegally access the permissions that have been previously granted to the app and run commands with administrator permissions. These attacks can be noticed by the user if it happens to him.
Other signs of malware activity: the battery goes empty faster than usual, your calls and messages do not reach their destination, and other overuses of the device’s resources.
What you should do: Know the app before you install them on your phone and download it from official sources, such as the Apple Store or Google Play Store. Check all the apps installed on your phone and know if something is not supposed to be there; maybe you didn’t authorize it in the first place. Check the app permissions and see to it that it is not charging you for online purchases that you didn’t make.
When installing and running apps, be careful with the permissions that you grant especially if it asks for administrator permissions. You may end up unable to uninstall the app through the system settings.
(See also: App Store Hack: WeChat and Other Apps Infected with Malware)
Sign #2. Your call and SMS logs include unknown numbers.
These unknown numbers may be international numbers that the malware is calling or sending messages to at your own expense. WeLiveSecurity.com identifies this type of malware under the Android/TrojanSMS family, which has been growing exponentially – about 50 new examples are detected every month and no signs of decreasing in the near future.
What you should do: Always check your call and SMS history so these unknown numbers won’t be running up your bill undetected. Don’t download from unofficial sources and be careful of the permissions you grant when installing apps.
Sign #3. Data usage has increased much greater than normal.
If you notice an excessive amount of data exchange even when you don’t use the device, there is a good chance of the presence of malware in the device. Malicious apps take advantage of your available data plan to exchange information with command and control centers operated by cybercriminals.
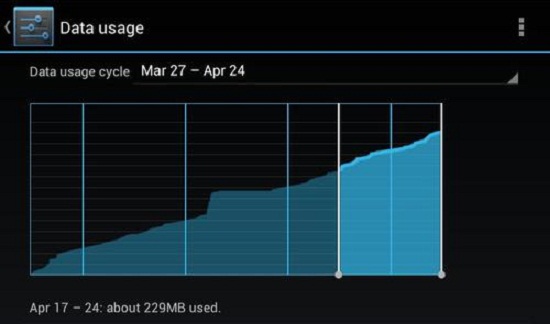
What you should do: Find out how much data your device has been devouring. For iPhones, tap on “Cellular”, then scroll down to “Cellular Data Usage”. For Android phones, swipe down from the top of the screen to bring up the notification shade. Tap on the top right corner gear icon, and then the “Data usage” icon.
(See also: KeyRaider Malware Affects Jailbroken Apple Devices)
Sign #4. The device sends and receives strange text messages.
Cybercriminals infect mobile devices by sending text messages that contain commands to be interpreted by the malware, which then takes the corresponding action. Lots of malware are able to delete such messages so they go unnoticed by the user.
The phone numbers in your contact list may also receive these test messages, and the recipient may unknowingly download the malicious content when they click the links.
What you should do: If you see these strange text messages, don’t just ignore them. Your device has a malicious app that has to be safely removed. If you receive a text message asking you to click a link, use common sense and don’t do it. And immediately inform the sender of this malware.
(See also: One Simple Text Can Hack 950 Million Android Devices)
Sign #5. You are getting charged for actions you did not make.
As mentioned above, there are malicious apps that make calls, send text messages, or use data without your knowledge. You’re in for a surprise when these show up on your phone bill. Your credit card data saved in your apps may also get stolen and used to make online purchases.
What you should do: It’s a must to identify malicious activity as early as possible so you can control these unwarranted charges before they pile up. If you can install a trustworthy security solution to scan our device, the better. They can identify if there’s a real threat in your device and they can also provide solutions to remove the treat.
Also, it is best to change your passwords immediately to bar any more entries from the malware if you suspect that sensitive information from your device has been compromised.
How to protect your device from malware attacks
Mobile technology should not be feared, and you should be able to enjoy the significant developments that it brings. But at the same time, you have to take a proactive and preventive approach to keep your data secure at all times.
- Update your device’s operating system and apps to the latest versions.
- Back up your data regularly.
- Download apps from official stores only, such as the Apple Store and the Google Play Store, to greatly reduce the chances of getting infected by malware.
- Use a screen lock and use a password or pattern that is hard to guess.
- Encrypt the content on your device.
- Avoid rooting or jailbreaking your device.
- Use security solutions from a trusted company.